Introduction
In the context of the rapid development of technologies and the constant rise of cyber threats, the security of information systems has become a top priority for organizations and individual users. Traditional authentication methods that rely solely on passwords often fail to provide the necessary level of protection.
Multifactor authentication (MFA) is a method of confirming a user’s identity that requires the presentation of more than one factor for access to a system or service. This method offers an effective solution to this problem by combining several means of verifying a user’s identity, such as knowledge (e.g., passwords), possession (tokens or mobile devices), and biometric data (fingerprints, facial recognition). This significantly enhances security and complicates unauthorized access to systems.
However, the implementation of MFA is associated with certain challenges, such as the need for additional investments, integration complexities, and potential inconveniences for users. The aim of this research is to analyze the development of MFA technologies and their impact on the security of information systems, as well as to identify existing issues and possible directions for further research in this area.
Main part. Core concepts and principles of MFA
As previously mentioned, MFA is a method of confirming a user’s identity that requires the presentation of one or more factors for access to a system. The main factors can be divided into three categories [1]. One of the most common factors is something the user knows – this can be a password, PIN code, or answer to a security question. This factor is traditionally the most vulnerable, as passwords can be stolen through phishing, data leaks, and other methods.
There is also a factor that represents something the user possesses – this can be a physical device, such as a mobile phone, token, or smart card. The user needs to have this device during authentication, which adds an additional level of security.
Another method of MFA involves something that is the user. This includes biometric data such as fingerprints, facial recognition, or iris recognition. Biometric methods provide a high level of security since they are unique to each individual.
The principle behind MFA is that, for successful authentication, the user must go through several levels of verification. This creates a multilayered defense, which significantly complicates the task for intruders. For example, even if a user’s password is stolen, access to the system will be hindered without the second factor.
Among the most common solutions based on MFA are one-time passwords (OTP) – passwords generated on the user’s device, sent via SMS or email, and valid only for a limited time. They reduce the risk of compromising account credentials, as even if an intruder gains access to the password, they will not be able to use the OTP, which expires quickly. There are also tokens and smart cards – devices that require the user’s physical presence. For instance, RSA tokens or YubiKey can be used in conjunction with a password. This significantly complicates the task for intruders, as they cannot gain access remotely [2].
The development of MFA can be divided into several stages. In the early 2000s, the focus was on passwords as the sole means of authentication. However, with the rise in cyberattacks and data leaks, the need for more secure methods became evident. During this time, technologies such as one-time passwords and tokens began to emerge.
According to a report by the FIDO Alliance [3], there has been a significant increase in the use of biometric methods from 2010 to 2017. This is attributed to improvements in technology and the availability of devices capable of performing biometric authentication (fig.1).
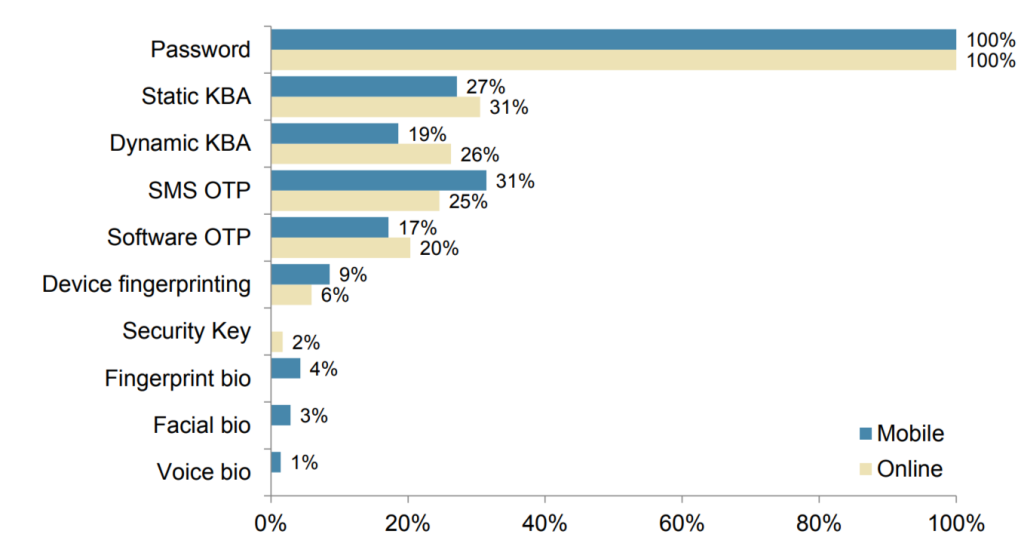
Figure 1. The ratio of different authentication methods from 2010 to 2017 [3]
Current trends in information security are leading organizations to increasingly favor comprehensive solutions that incorporate multiple authentication methods. For example, contextual authentication, which takes into account the user’s location, device type, and access time, is becoming more popular.
Moreover, the rise of mobile devices and cloud services is driving demand for solutions that ensure data security without compromising the user experience [4]. This creates a need for the development of more user-friendly and intuitive interfaces for authentication.
The impact of MFA on the security of information systems
Technologies MFA significantly enhance the security of account credentials and systems. However, some authentication methods have their vulnerabilities that can be exploited by malicious actors. For example, the transmission of one-time passwords (OTP) via SMS is susceptible to man-in-the-middle (MITM) attacks and interception. According to guidance from the Cybersecurity and Infrastructure Security Agency (CISA), SMS and voice calls are not recommended as secondary factors due to the vulnerabilities of communication protocols [5]. The report also emphasizes that even with MFA in place, phishing attacks can be used to trick users into providing a second form of authentication.
Social engineering remains one of the most effective methods for bypassing MFA. Attackers can employ phishing techniques or fake confirmation requests to deceive users into providing additional data. For instance, in cases involving push notifications, users sometimes automatically approve requests without verifying their authenticity, which attackers can exploit [6].
Incorporating biometric data into authentication systems introduces a distinct set of risks due to the unique and permanent nature of this information. In cases of a biometric data breach, the consequences can be far more severe and lasting than with other forms of authentication, such as passwords. Unlike a password, which can be reset or changed in response to a security compromise, biometric data – such as fingerprints, facial recognition, or iris patterns – are intrinsic and unalterable attributes of an individual. This limitation creates a long-term vulnerability, as compromised biometric data cannot be «reset» in the traditional sense, leaving affected users at perpetual risk of identity misuse. Consequently, while biometrics offer a high level of security, the potential for irreversible impact in the event of a leak necessitates additional safeguards and secure handling protocols for these sensitive identifiers.
The use of MFA based on hardware tokens and biometrics requires protection at both the device and software levels. Recent studies show that vulnerabilities can arise in the devices themselves, such as in tokens or biometric authentication devices, necessitating constant software updates and monitoring for potential threats. To better understand the strengths and weaknesses of various authentication approaches, the following table 1 provides a detailed comparison of authentication mechanisms for personal devices and online resources.
Table 1
Comparison of authentication mechanisms for personal devices and online resources [7]
| Criterion | Personal devices | Online resources |
| Types of authentication factors | Password, biometrics, PIN, token. | Password, one-time code (OTP), biometrics, push notifications. |
| Ease of use | High for biometrics and PIN; moderate for passwords. | High for push notifications; moderate for OTP and passwords. |
| Security level | High with biometrics; moderate with PINs and passwords. | High with two-factor authentication; moderate with passwords. |
| Susceptibility to attacks | Physical access can simplify a breach. | Phishing, MITM attacks for passwords and one-time codes. |
| Advantages | Fast access, no reliance on network connection. | Enables remote authentication, user-friendly. |
| Disadvantages | Risk of device loss; vulnerability in case of data theft. | Potential compromise via phishing and data interception. |
| Frequency of updates | Not required for biometrics; necessary for passwords. | Regular updates to enhance security. |
| Examples of Solutions | Touch ID, Face ID, PIN codes, physical tokens (YubiKey). | Two-factor authentication, OTP, push notifications. |
Although MFA significantly enhances security, it is important to remember that it is not a universal solution. To maximize its effectiveness, organizations should implement additional security measures alongside MFA, such as regular monitoring of authentication logs to detect any unusual login patterns. Policies for prompt response to security incidents, including immediate revocation of compromised credentials, are also essential. Moreover, integrating MFA with other protective technologies, like secure access gateways and encryption, can help further protect sensitive data.
Prospects for the development of MFA in the context of digital transformation
The rapid digital transformation across various industries has created new challenges and opportunities for enhancing the security of information systems. MFA is increasingly recognized as a critical component in building secure digital infrastructures, and its future development promises to address both security demands and usability challenges within this evolving landscape [8].
One of the primary trends in MFA development is the shift towards passwordless authentication. Traditional password-based methods, long vulnerable to brute-force attacks, phishing, and poor management, are gradually being replaced by solutions that use biometric verification, device-based identification, and cryptographic keys. These innovations streamline the authentication process while effectively reducing risks related to password misuse and theft. With entities like the FIDO Alliance promoting standards for passwordless technologies, these methods are anticipated to gain traction, particularly in sectors requiring high security, such as finance, healthcare, and government.
Artificial Intelligence (AI) and Machine Learning (ML) are playing an increasingly central role in MFA, enhancing adaptability through what is known as adaptive authentication. By evaluating contextual data – such as user behavior, device location, and network conditions – AI-driven MFA systems can analyze patterns and detect anomalies to adjust authentication requirements based on perceived risk. This approach not only strengthens security but also maintains a user-friendly experience, particularly valuable in detecting sophisticated threats and dynamically adapting to diverse user environments.
Biometric authentication is also advancing rapidly, with new technologies such as voice and gait recognition emerging alongside more traditional methods like facial recognition, fingerprint scanning, and iris recognition. Multi-biometric systems, which combine two or more biometric factors, offer higher accuracy and security by overcoming the limitations of a single biometric modality. These advancements address existing challenges, such as privacy concerns and spoofing vulnerabilities, through secure encryption, dedicated storage, and enhanced liveness detection, potentially expanding biometric applications across a range of sectors.
In addition to biometric innovation, blockchain technology offers promising potential for decentralized MFA solutions. Blockchain’s distributed ledger can store identity verification data in a secure and transparent manner, removing reliance on a central authority and significantly reducing the risk of single points of failure. Decentralized authentication systems built on blockchain could enhance user privacy while providing a tamper-proof method of verifying identities across multiple platforms. This development may also facilitate interoperability across different MFA systems, laying the groundwork for a unified digital identity infrastructure. However, to realize the full potential of blockchain-based authentication, efforts toward standardization and collaboration will be essential.
The development of MFA technologies also includes a stronger focus on user-centric security, particularly as the demand for intuitive, accessible security solutions grows. Usability remains a critical factor for the adoption of MFA, especially in the consumer sector, where users may resist overly complex authentication procedures. Future developments are likely to prioritize streamlined experiences, minimizing authentication steps while integrating MFA directly into user devices and applications. For instance, wearable devices and continuous biometrics may provide seamless verification throughout a session, enhancing both security and user convenience.
As digital threats evolve, hybrid MFA systems that combine different authentication factors offer increased flexibility and a more adaptive security model. This approach allows organizations to implement customized security protocols tailored to varying levels of risk, user preferences, and specific situations, thereby ensuring both security and scalability. Hybrid MFA systems that incorporate both on-premises and cloud-based elements are well-suited for organizations with diverse security needs, enabling modular architectures that can adapt to emerging threats.
Conclusion
The development of MFA technologies significantly impacts the enhancement of information systems’ security. MFA provides reliable data protection by combining several identification factors, thereby making unauthorized access more difficult. Although the implementation of multi-factor authentication requires additional investments and may present some challenges for users, its advantages significantly outweigh potential drawbacks.
Analysis of existing solutions has shown that a combination of different authentication factors, including one-time passwords, biometric data, and tokens, provides layered security. However, to counter the growing cyber threats, organizations must not only utilize MFA but also implement comprehensive security measures, such as regular software updates and user training. In conclusion, it can be noted that multi-factor authentication continues to evolve, and further research in this area will focus on improving and enhancing the user experience without compromising security.
References
1. Mwaheb A. Blockchain-based multi-factor authentication: A systematic literature review // Internet of Things. – 2023. – № 23.2. Sidorov D. Asynchronous programming techniques and their impact on user experience in modern web applications // Znanstvena misel journal. – 2024. – № 94. – P. 62-65.
3. The-State-of-Authentication-Report / Fido Alliance // URL: https://fidoalliance.org/wp-content/uploads/The-State-of-Authentication-Report.pdf (date of application: 03.10.2024).
4. Dudak A.A. Review of approaches to the development of scalable project management systems based on modern frontend technologies // Trends in the development of science and education. – 2024. – No. 113(6). – P. 22-25.
5. Multi-Factor Authentication / CISA // URL: https://www.cisa.gov/sites/default/files/publications/cisa-multi-factor-authentication.pdf (date of application: 07.10.2024).
6. Kanojia B. Authentication Bypass Through Social Engineering // Cybercrime in Social Media. – 2023. – 1st Edition. – P. 20.
7. Mohammed A. H. Y., Dziyauddin R. A., Latiff L. A. Current multi-factor of authentication: Approaches, requirements, attacks and challenges //International Journal of Advanced Computer Science and Applications. – 2023. – V. 14. – №. 1.
8. Kantipudi R., Mallavarapu A. S. K., Rajagopal S. M., Kagolanu M. A Comprehensive Analysis on using Multifactor Authentication System for Three Level Security //2024 2nd International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT). – IEEE, 2024. – P. 498-503.
